Job Position: Senior Hybrid Mobile App Developer
Description: Build innovative software products using Hybrid Mobile app platform.
Experience: 3-4 Years
Job duties and responsibilities:
- Understand requirements, assess the feasibility and provide time estimates on implementing new features and functionalities.
- Use best practices to deliver high-quality code; Unit-test code for robustness including edge cases, usability, and scalability.
- Discover and evaluate new technologies to maximize development efficiency and handhold the client by recommending the benefits.
- Collaborate with the design team to bring creative ideas to the mobile UI and craft a beautiful Android/iOS user experience.
- Work as part of a team-building prototype, applications, and user experiences.
Job requirements and qualifications:
- Work on software architecture and development of Hybrid Mobile applications and communicate technical limitations/roadblocks to the team.
- Skill Sets on technology aspects: HTML5, CSS3, AngularJS, Angular, React Native, IONIC, Cordova, Deployment apps in iOS and Android
- Familiar with RESTful APIs, UI Kit, offline storage, threading, performance tuning, and all UI components in the Android/IOS object library foundation.
- Candidate should have experience in Xamarin and also exposure in other hybrid mobile development like Native Script and others
- Work on 3rd party libraries, cloud message APIs, and push notifications.
- Understand Androids/Apples Human Interface Guidelines and other UX & UI standards to create scalable products.
- A knack for benchmarking and optimization by identifying bottlenecks and limitations in application development.
- Integration of 3rd party API's like Biometric GPS, Maps etc.,
Role: Lead Programmer
Work Location: Hyderabad
Industry: IT – Software
Qualification: B.Tech/MCA
Work Location: Hyderabad
Experience: 2-6 yrs.
Job Description:
- Must have the ability to run scrum team of developers via Agile delivery method.
- Ability to lead the team on best code practices, design, deployment and technical release
- Participate in Technical Design activity across the various technology domain specific teams involved to ensure that the overall Technical Design is complete and in line with Non Functional Requirements, Solution Architecture and System Functional Design specifications
Required Skills:
- Core Java (Java 8/11)
- Enterprise Java (JEE) & transaction processing
- Spring Framework & SpringBoot
- REST/SOAP web services
- File processing and transfer protocols (SFTP, SSH)
- Messaging
- Strong experience in JavaScript, ReactJS & Angular, HTML 5, CSS.
- Strong knowledge and expertise of cyber security principles (during handshake, authorization & authentication, data in transit and data at rest), encryption methods best practices and options
- Relational databases, stored procedures, stored functions, sql language
- Git, Maven, CI/CD, Docker, Ansible
- Good knowledge and understanding of financial transaction processing principles and technical requirements
- Excellent understanding and knowledge of solution and architect design best practices and approach
- Good knowledge and understanding of Service Oriented Architecture
- Excellent knowledge of application for scalability, security , performance and design for future demands
- Experience in Test-Driven Development (TDD)/Behaviour-Driven Development (BDD
- Strong knowledge of Automated build and deployment, Continuous Integration
- Must be hands-on and have the ability to perform reverse engineering and to understand code modules and execute existing code.
- Desire to continuously improve craft of software development while adhering to best practices and standards.
- Excellent communication, organizational and problem solving skills.
Job Description:
1. Master/Advanced Professional (A2019 or AA v11) certified RPA Developer
2. Must have worked on Task bot , Metabot & IQ bot development
3. Should be well versed with A2019 Control room operations
4. Experience in Web & Window application automation
5. Preparing & maintaining of PDD & SDD documents
6. Should be a self-starter with debugging & analytical skills
7. Experience in preparing RPA Unit test cases and testing RPA bots
8. Development knowledge on .Net, C# or Python or JAVA is a plus
Experience: 2-5 Years
Job Description:
- Evaluate the functional and non-functional requirements for test-ability, and use suitable cases for automation
- Develop/build test automation strategy and focus specifically on maximising reusability for regression
- Design, build and execute automated tests to validate data centric applications
- Identify regression testing needs and create and maintain an Automated Regression Suite
- Provide test execution reports
- Work closely with architects to analyse the end-to-end scenarios, gather requirements, and design the test cases that needs to be automated
- Maintain automated scripts utilising the existing framework, adhering to coding standards
- Suggest/explore alternate tools for automation to bring-in more productivity and coverage
- Participate in troubleshooting and drive root cause analysis and resolution
- Trained Fresher in Test automation tool primarily using Java with Selenium
- Deep understanding in developing test scripts using tools like Selenium
- Proficient in database fundamentals and exposure to complex SQLs. (Oracle/MySQL)
- Knowledge on source control management tools (GitHub, Jenkins)
- Knowledge with using Agile lifecycle management tools like Jira
- Comfortable with frequent, incremental code testing and deployment
- Qualification: B.Tech
- Designation: Quality Analyst
- Experience: 2-5 Years
Job Description:
- Evaluate the functional and non-functional requirements for test-ability, and use suitable cases for automation
- Develop/build test automation strategy and focus specifically on maximising reusability for regression
- Design, build and execute automated tests to validate data centric applications
- Identify regression testing needs and create and maintain an Automated Regression Suite
- Provide test execution reports
- Work closely with architects to analyse the end-to-end scenarios, gather requirements, and design the test cases that needs to be automated
- Maintain automated scripts utilising the existing framework, adhering to coding standards
- Suggest/explore alternate tools for automation to bring-in more productivity and coverage
- Participate in troubleshooting and drive root cause analysis and resolution
- Trained Fresher in Test automation tool primarily using Java with Selenium
- Deep understanding in developing test scripts using tools like Selenium
- Proficient in database fundamentals and exposure to complex SQLs. (Oracle/MySQL)
- Knowledge on source control management tools (GitHub, Jenkins)
- Knowledge with using Agile lifecycle management tools like Jira
- Comfortable with frequent, incremental code testing and deployment
- Qualification: B.Tech
- Designation: Quality Analyst
- Experience: 0-2 Years
Designation:
1.Good knowledge on Core PHP, MySQL, HTML, Javascript, JQuery, CSS etc.
2.Basic Working Knowledge on any one PHP Frameworks like codeigniter, Laravel, Cake PHP, Zend, YII etc.
3.Must have strong knowledge on Wordpress content management system.
4.Good knowledge of relational databases, web services.
5.Strong communication skills and excellent listening skills.
6.Exposure to Agile Methodologies and Good understanding of SDLC.
7.Ability to work in a team as well as an individual.
• Qualification: B.Tech/MCA
• Designation: PHP Developer
• Experience: 1-3 Years
• No Of Positions: 1
There’s no denying that technologies are shaping the future and a lot of it is surrounding artificial intelligence (AI) and machine learning. Think about any three platforms that you use daily? Be it Google, Facebook and just about every platform are knee-deep in these technologies and there is some tool you should definitely try today.
Tool #1: Import.io
Import.io is a perfect tool for anyone interested in the conversion of semi-structured information into structured data. This includes machine learning, data-driven marketing, price monitoring, and much more.
This tool offers real-time data retrieval and integration with many common programming languages and data analysis tools.
The features highlighting data extraction include:
• Extraction of images
• Extraction of prices
• Extraction of web data
• Extraction of the Phone number
• Extraction of IP Address
• Extraction of Email Address
Pricing: Includes a free trial and a free version for each user after which the starting price is $299.00/month/user
Tool #2: X.ai
Is it chaos to arrange and schedule meetings? Well, not anymore! X.ai is a simple and effective tool based on artificial intelligence. This tool has an AI scheduler that makes arranging appointments and meetings effortless.
This autonomous scheduler can schedule meetings just about anywhere which includes:
• In your Inbox
• AI Engine which learns exactly when, where and how long you like to meet
• In your calendar, for every time there is a last-minute change in the plans
Pricing: There is a free trial for 14 days after which the starting price is $8/month/user.
Tool #3: Grammarly
This tool becomes a go-to partner for anyone who wants to write error-free! Grammarly uses AI proofreading to avoid embarrassing typos and grammatical errors. Grammarly compiles a report of your most common mistakes so that you become a better writer over time.
Fabulous isn’t it?
Moreover, one can choose their writing goals based on the intent, audience, formal/ informal writing style, emotion or domain, and Grammarly provides insights based on the goals selected by the user.
Pricing: One can use the basic writing correction plan for free. On the other hand, the premium versions include advanced writing feedback for individuals starting from $11.66/month if billed annually.
Tool #4: Uberflip
Uberflip is a complex AI tool which delivers an advanced platform for content personalization that helps to create unique experiences for each customer. This tool is a perfect fit for enterprises who want to improve their content experience and the buyer journey.
Uberflip helps to ignite meaningful relationships by creating, managing and optimizing content experiences with a remarkable experience at every stage of the buyer’s journey.
The AI engine learns what content performs best and makes recommendations to reduce bounce rates and increase engagement.
Pricing: There is a free demo after which Uberflip offers a customized price depending on the features included.
Create More
The tools that we’ve looked at in the list help you to do more by automating tasks, crunching data at scale and spotting patterns to create a more efficient marketing process.
IoT Devices:
IoT devices are the innovative creation of human beings to give us a luxury lifestyle. From research, 7.2 billion people are present on Earth and around 20 billion smart devices are used by humans. Since 2015, the demand for IoT devices is rapidly increasing. It is found out that a huge number of IoT headquarters are present in the USA and also the people of western countries are adopting this technology.
Let's concentrate on the following sectors where IoT works best.
- Wearable
- Smart homes
- Vehicles
- Manufacturing
- Supply chain
- Agriculture
- Healthcare
- Energy
Top 10 IoT devices:
1. Google smart home:

Google smart home voice controller has a lot of interesting features. You can start your day with it. You can plan and track your day as per your wish just with your voice. You can manage alarm, media, lights, volume, planning, and entertainment automatically within a second.
2. Amazon dash button:

Amazon dash button is a small IoT device which is used for ordering consumer goods through online. It has a barcode scanner as well as a voice command device. Generally, it helps the house owners to reorder the necessary product that they use frequently. This must be configured to the particular item that needs to be frequently ordered. By linking to a Wi-Fi signal, you can do all these processes.
3. Amazon echo plus voice controller:

Again, Amazon's echo plus is a very good Amazon IoT product that helps you achieve control over your home. To get your job done, you can offer the device voice command. For you, it can play music and also connect to external gadgets such as speakers or headphones.
4. Kuri mobile robot:

Kuri is a famous, tiny and adorable home robot. When you give a command, it will follow directions. It is generally intended to capture your everyday moments in your home. It has a sensor touch and HD camera to capture the moments and with its evolving colour, you can also understand its state of mind.
5. Doorbell cam:

The intelligent doorbell cam is an innovative IoT invention that helps homeowners by notifying them when visitors arrive at the doorway or pressing the doorbell. It enables owners to watch the visitors and speak to them. Some smartphone apps can make it possible nowadays.
6. Smart light switches:

Smart light switches allow you to remotely control the light of any room (anywhere) via a smartphone application. Your light should be connected to the Wi-Fi network, so you can only do that. You can also alter your choice of light colour. Easy to install and restart.
7. Smart Lock:

A smart lock is also a commonly used IoT tool to prevent strangers from keeping your home secure. These devices are designed to allow you to access it from anywhere without any trouble. It also provides you with the update, whether or not the gate is successfully locked. If the door is not locked accurately, then you can lock it right away through the mobile application. There’s no chance of missing the keys. When approaching the gate, the smart lock can feel the presence of the user.
8. Air pollution monitor:

Air pollution monitor measures the purity of the air that we breathe. It enables us to identify the polluted region and it shows all the information related to air pollution.
9. Easy temperature control:

This smart temperature control enables smart temperature controlling according to our daily routine. It has so many smart features to control the temperature remotely. It saves energy and compatible with a lot of other devices.
10. Smart plug:

Smart plug allows its user to automatic turn on/off the devices remotely from anywhere. Installation is very easy and is compatible with many other devices like Alexa and free voice control from Google.
Business Process Management always plays a key role in establishing an organized working culture and strategized business actions irrespective of the size and scope of any organization. It eases the business operations and enhances the growth of financial planning with ensured results. Also, provides clear cut transparency of all the working modules inside and outside the organization.
A completes guidance of business understanding, documenting, structuring, modeling, managing, and monitoring is laid down by the business process management which simultaneously increases the value of financial assets.
Besides all the boons, BPM also comes with a set of challenges to overcome in order to endure the complete fruits of the model implementations. Everything needs to be assessed and understood properly before taking a key decision. One thing, which is commonly missing in practicing the BPM model is the failure to correlate and collaborate all the actions under one roof, in short, the lack of governance is the main challenge here.
In this regard, we would like to portray the top challenges faced by present-day organizations while implementing BPM. The commonly faced challenges are classified mainly into three different levels…Strategic Level, Technical Level, and Operational Level.
#1. Challenges faced at the strategic level
-
No process defined
BPM model has its own roadmap designed, which is misunderstood by most the organizations during the initial level itself and there is no proper guidance with professional experience in enhancing the new user to understand the functionality and scope of BPM models. There should be a well-defined approach drafted predominately so that new users can adhere to it without committing major mistakes.
-
Different opinions or mindsets
People or the resources with different mindsets cast their own opinions which deviates the actual flow of BPM, which results in confusion regarding which functionality to implement first and what should be the priority order to follow next. Preconceived expectations and understanding also lead to the absence of a unique mindset in practicing the BPM models.
-
Lack of control or governance
There is no proper or centralized control or guidance in designing the new functionalities or planning new activities using BPM technologies or workflows. Every single module has its own author and owner, which results in a lack of central monitoring.
-
Missing customer satisfaction
The end-users or the customers using the BPM models always complain about the scope and scalability of BPM projects. Everything needs to be customized and optimized before implementing the right model your organization wants to fit in.
#2. Challenges faced at the technical level
-
The communication gap between strategic and technical levels
There is a dire need for a standard channel between the strategic and technical levels of the BPM model to establish proper communication to know about the progress of each functionality. The lack of proper integration between these two levels can also result in bad positioning of BPM investment.
-
Lack of common or standard practice
This is the major cause of the limited benefits of the Business process management model, which is restricting the future enhancements and progressions of the model. This results in unwanted pain points and unnecessary re-work of the existing models which is no way helpful to the business heads.
-
Complex process identification
Due to the absence of proper communication model between different modules, there are high chances to ignore the complex process identification as soon as they are triggered or demands attention. This directly lunches in threat welcoming or process failure.
-
Failure of life cycle management
Vendors have their own methodologies to implement in BPM, based on their past experiences or project related R& D work. But, there comes a time, when there is no proper guidance to the newly implemented lifecycle management techniques to understand their scalability factors.
#3. Challenges faced at the operational level
-
Lack of integration and collaboration
At the high end of an operational level, we always speak of integration and collaboration as the key roles in accomplishing any task, which is a drawback in complex BPM models. We have to address this kind of high priority challenges at the earliest, in order to ensure the increase in overall product performance.
-
Implementing the right product functionality
As BPM has a very large complex of models and sub-models functioning altogether, it becomes hectic in identifying the right potential functionality for each and every activity performed. Hence care should be taken to carefully assign proper key roles to every module with a though research and analysis.
Conclusion
By addressing each and every challenge within the same level of implementation can yields better results and provide clear tile visibility of all the process flows by establishing a standard mode of communication and functioning by adhering to the below mentioned best practices without fail…
• Always balance the terms between efficiency and its worth
• Plan your timelines well in advance in completing a task
• Know your limits and challenges
• Establish a standard mode of communication
• Evaluate both inner and outer difficulties and fix them as soon as possible
• Measure the profess and manage the business values
Right actions always lead to the right decisions benefitting both the business leaders, stakeholders and the end-users with prosperity.
Open source tools take to play a major role in defining your project scope and after deployment progress. In fact, the finances come down drastically when you choose to opt for open source tools and technologies instead of paid tools and technologies.
Whether it is a document management system or a development framework for any required business application system, open-source solutions provide you with the best tailor-made infra to design, develop and deploy your needs.
There are many benefits in using the open-source tools and technologies like no need to follow the regular updates and version changes, it happens automatically. All the technical trends are always taken care of. So, it is obvious that the stakeholders always tend towards using the open-source tools and seek a benefit of interest from them.
There are a lot of open-source tools available in the market catering different needs and requirements like from machine learning to web servers, automating the testing script, designing the source file, etc, it is in the hands of the developer to choose the perfect tool for addressing the requirements in order to prevent the future hitches.
In this regard, we would like to shed some interesting factors to consider while choosing your right open-source tool and what the points to remember in selecting one are.
#1. Check the initial requirements
- Is the software a licensed one?
- Is it easy to install?
- Is it easy to run?
- Are the issues and PR raised?
- Is the contributing doc provided?
- Does it have a docker file?
- Does it support tests?
- Does it have badges?
#2. Check for the license type
Open source tools come with different license types and different potential values. One should never miss checking the license type before opting for the tool of his choice. Permissive license is the best option to utilize your complete freedom in writing or developing the code. So, it is always advisable to choose the permissive license type open-source tools and technologies.
Also, there is also a copyleft open-source type of license, which comes with restricted permissions. So depending on the scope of your source code, choose the license type here and always be ever ready to counter the legal issues.
#3. Security assessment
Open source tools and technologies are always prone to high threats and exploitations easily when compared with others…so, it is advisable to stay alert in identifying the different behavior and only trust those tools which have a well-supported team in fixing the vulnerable patches as soon as they are unveiled. CVSS V3 is a scoring system, which assesses the severity of open source community and provides the score of vulnerability rate so that we can make a decision based on the given information in choosing the right tool.
#4. Support
There are two major roles that play a vital role in supporting open-source platforms. One is based on individual interests, who are readily offering their skill set to improve the efficiency of the tool and the others, known as dedicated contributors, provide their services for free and market their expertise indirectly by offering a paid long term support for the beginners, to implement the open-source tools and technologies in a better way.
#5. Policy
Always have an eye regarding the policy factors of any open-source tools and technologies. It plays a vital role in enhancing the standardization of tools usage and implementation of related technologies. Seek the opinion of direct dependency roles of open source tools, in order to understand the scalability of stakeholder scope while coding, designing and deploying various projects.
#6. Ease of documentation
The documentation of the open-source tool must be easy to understand and readily accessible to everyone. The contributions of the community by both the freebase users and committed users help to maintain the stability of the platform and also reflect the recent changes in the document without fail. So, take care of choosing the tool, who is highly active in updating their documentation on a regular basis.
#7. End-user profile
Cross-check on the list of end-users who are actually implementing the particular open-source tool which you want to choose. The list can directly reveal the potential and the technical capability of the tool if the renowned company names are on the list and hence you can go ahead with a positive sign without doubting the security and endurance of the tool.
#8. Activities of community
An open-source community always has an active community where both the contributors and end-users play a key role in the activity sharing to enhance the forums, blogs, and messaging applications to share their experiences regarding the usage of the software as well as the issues rose at the same time. Check for such a community where the queries are addressed within in short span of time with high priority and the security patches are fixed in a timely manner.
Conclusion
Always check twice and rethink before choosing any of the available open-source tools. It is obvious that they are so attractive to see because of their benefits and the low cost of investment and maintenance. But, one should be careful choosing the best fit in addressing their requirements by considering all the above factors.
An initial check on these five factors helps to establish a standard working model in the future, without the unexpected hassles and worrisome issues that can bring down your working performance.
Imagine the present Digital world without the use of Computers…..Can’t, right? We are entirely dependent on computer usage either directly or indirectly to address both our personal and professional needs. But the fact is that there is always a high-risk exposure awaiting to thrash our systems and conquer the entire information without authentication by just injecting a small piece of malware into our systems.
Malware is a piece of code intended to harm the residing resource. Understanding and analyzing every aspect of a given malware like its origin, functionality, and the impact under special conditions can be coined as the definition for malware analysis. It is highly recommended to assess malware behavior and take the respective preventive measures.
Need for malware analysis
- To examine the malware behavior
- To determine the damages that can be caused
- To identify the cause of vulnerability
- To analyze and define the compromising indicators
- To analyze the impacts of the attack and identify the primary victim.
Types of malware analysis
Malware Analysis can be generally categorized into three different categories, as shown below.
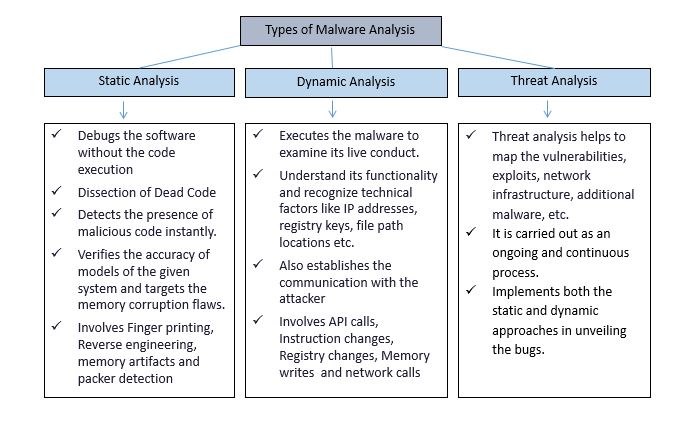
Static malware analysis techniques
#1. Analysis of memory and operating system
The memory and the operating systems must be thoroughly checked and verified frequently to investigate the new entries.
#2. Virus scan
A virus scan must be performed every time a new program or software is installed. Ensure to use only updated malware detecting software.
#4. Identify the Windows executable files
Examine and identify all the executable files residing in windows along with the associated compilers.
#5. Automate dis-assemblers
The Dis-assemblers can automate the code in a reverse manner and also upgrade its security levels.
#6. File fingerprinting
Always ensure to fingerprint the files so that the value changes can be identified easily and quickly.
#7. Identify the packed code
Never ignore the packed code existence and try different identifying software to detect it. Completely bifurcate the point and click packers as they lay the path to the intruder to take control of the system.
#8. String analysis
Every string must be deeply analyzed to know its purpose function and where it is located in the file.
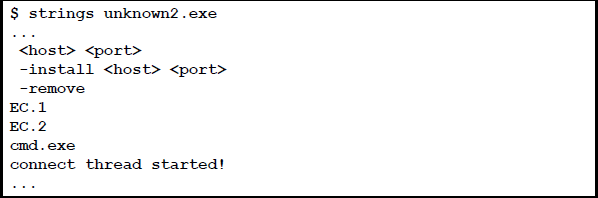
#9. Safeguarding web search
Be careful with the IP addresses, different domain names, network issues, and email addresses while browsing, and avoid any imprudence with malicious code.
Dynamic malware analysis techniques
#1. Monitoring process and filtration
Process monitoring helps us to find the key attribute information like thread activity, process time, file activity, and registry activity. Filtration plays a vital role in monitoring.
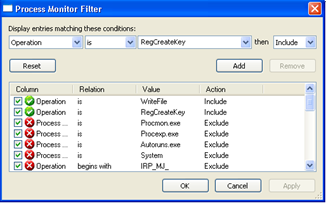
#2. Analyze the network traffic
The next key factor of dynamic analysis is to detect the network traffic and to determine the prospects of it.
#3. Analyzing PE structure
Examine the PE file to identify interesting fields of code.
- .text: This contains the executable code.
- .rdata: This section holds read-only globally accessible data.
- .data: Stores global data accessed through the program.
- .rsrc: This section stores the resources that are required by the executable.
#4. Debugging
Dynamic linking and debugging always benefit in the early identification of malware and helps to attain protection.
Automation has also crept into the quality assessment by elevating its standards and also helped for effective testing with the most modern approaches. QA automation especially led to the enhancement of the final product performance much easier than ever. Bug identification and Bug fixing can be done very smoothly with the specified automation tools. The market is equipped with many Test automation tools which are best in their perspectives. Every organization has a different approach in performing the quality check, and various tools and methodologies are implemented and sometimes invented too.
We proudly say that Eclature expertise crown is equipped with a jewel of QA to help our customers to test and maintain the quality of their products and services with utmost trust and dedication. We have a well-trained and skilled professional Quality Analyst team who are highly smart and efficient in using the Automated Testing Tools.
Let us focus on the way and approach our QA team follows in attaining 100% quality assurance.
Testing services
We aim to achieve quality customer experience with the most advanced testing mechanism. Our approach towards accessing the quality includes the mechanism which speaks efficiency.
We always implement well-defined mechanisms when it comes to auditing of any process. Our QA team follows the standard STLC approach customized in our way of testing different software applications.

#1. Requirement/ design review
A well organized and planned team meeting with the respective client is conducted regularly until and unless all the test requirements are gathered from the software application. We make sure that the client is involved in every aspect of the testing process to improve the quality assessment by taking constant feedback from them.
#2. Test planning
One all the required inputs for test design are gathered, we move on to design the Test plan which explains how we carry out the testing phase of the respective application like hat technologies must be used, resources, entry and exit criteria, etc.
#3. Test design
One all the required inputs for test design are gathered, we move on to design the Test plan, which explains how we carry out the testing phase of the respective application like hat technologies must be used, resources, entry and exit criteria, etc.
#4. Test execution
- Test-Driven Development (TDD) and Behavior Driven Development (BDD) testing, are implemented by using the Frameworks of Selenium WebDriver tools like Geb & Spock and Protractor.
- SoapUI & RestAssured are used for Web services testing (SOAP & REST)
- Load Testing is carried out with JMeter
- Jenkins is used to building and enhance the Configuration and Automation process.
- AWS (Amazon Web Services) tool is also utilized in case of testing the cloud-based applications.
- We use different simulators to check mobile apps.
#5. Test reporting
A perfect reporting and updating the identified bugs help to fix bugs immediately, which results in the accelerated performance of the application. We use specific tools such as to control the flow and mechanism of the testing phenomena.
The entire testing life cycle is carried out from the customer’s perspective, and we make sure that our methodologies are highly transparent and easily customized as per client requirements.
Security is not just a defense mechanism, but it is a matter of trust and dependence.
The new competitive age of digitization is seeking more attention due to the increasing rate of cyber threats. It is highly essential to safeguard the hardware devices before the software systems as the black hat hit rate is equally threatening to both software and hardware devices and take the calculated steps to bring up the digital mutiny.
In this perspective, let us shed some light on what happens if hardware security is ignored.
- Manipulations are carried on the system’s input and output functions
- Sensitive data is vulnerable to malware attack
- Software security is not enough ensured against cyber attacks
Sometimes we cannot even imagine the amount of loss incurred when a proper hardware security system is not installed. So, it’s high time that we start focusing on securing our Hardware as equally as we concentrate on software security.
What is hardware security?
Cryptographic Engineering is the baseline cause for the origin of the term Hardware Security. Ensuring the physical security which cannot be easily obtained by the software is the main reason for focus here. But, when it comes to a professional definition, securing over-all physical attributes like design, keystrokes, access controls, speed, power consumption, supply chain management together with crypto processing is called as Hardware security.
The entire securing process can be attained by using a physical HSM (Hardware Security Module), which is either plugged in or attached to the computer systems. The HSM performs the entire cryptography life cycle process, which includes provisioning, managing, storing, and disposing mechanisms. Some listed features of using the HSM’s are:
- Provides high alert security
- Encryption and Decryption procedures
- Digital signature protection
- Message Authentication codes
- Keystroke management
- Verifies the data integrity
- Accelerates the SSL connections and smart key generation
Types of Hardware Security Modules and their Applications:
The HSM’s are internationally certified modules that promise to provide unbreakable security walls and also validated successfully with FIPS 140 Security Level4 security standard. Such HSM’s are aiding the digital security systems with the following applications
#1. CA HSM
The Certification Authority (CA) HSM is widely used in the Public Key Interface environment to manage the entire asymmetric keystrokes and sensitive data. It helps in protecting the logical information with specific security measures and also performs the auditing of logs. Even the keystroke information is also bagged with a strong backup.
Applications: Networking Systems, Industries, General systems, E-Platforms, etc.
#2. Bank HSM
A unique and specially designed HSM’s are used in all the payment systems nowadays. These are designed to support all the banking or other financial transactions with highly defined security terms. They help in verifying the user identity to validate the entered PIN each time. Encryption mechanism is also carried out in the entire transaction process with enhanced secure key management.
Applications: Banks Systems, Financial Organizations, Online Payments, Money Transfers, etc.
#3. DNS SEC
This HSM manages the Zone file signatures and handles the sensitive information.
Applications: Digital Signatures, Confidential Information Gathering, Security Agencies, etc.
#4. Cryptocurrency wallet
The HSM aims to bestow the guaranteed cryptocurrency transactions by storing and managing both the public and private keys.
Applications: Bitcoin, Ethereum, Dogecoin, etc.
#5. Establishing an SSL connection
The concerned HSM engineers the performance of HTTPS protocols and increases the speed of SSL connection by eradicating the unwanted RSA operations. Also, Keystroke management is handled in this type of HSM.
Applications: All HTTPS protocols.
Importance of Maintaining Hardware Security
Proper maintenance of hardware security is a much-needed concern and should be taken on a serious note to break down the speed of physical cyber-attacks. Any weakness, either in keystroke or other related physical devices such as routers, CPU’s, etc., can attract and invite the multiple attacking modes to invade.
For example, let us consider a Side-Channel attack and Power Glitch attack, which directly conveys a message stating what happens when we ignore hardware security.
Side-Channel Attack:
This attack mainly concentrates on the technical information of the system’s internal structure and then starts to implant the violations in it. The gathered information includes the System Timing, Keystrokes, Power consumption, electro-magnetic leaks, and sound system. The side-channel attack has different forms of attacking modes and can be triggered at any point in time once the system’s information is stolen. The listed ones are:
- Power-Monitoring Attack
- Timing Attack
- Cache Attack
- Electro-Magnetic Attack
- Sensitive Data Theft
Glitch Attack:
A glitch can be defined as a suspicious attack on the performance of any device. Targeting the consumption features of the device and altering it with the malware inputs, which results in the machine break down, is referred to as being a glitch attack. Manipulating the device power, time, and memory inputs are the main motto of the attacker here.
- Clock Glitch attack
- Power Glitch attack
Conclusion:
Hence, hardware security must be given the top priority to ensure highly secured transactions or communications in the present digital environment. The easiest tip to tackle hardware security is to use the most suitable and effective HSM without fail.
A safe and secure digital environment is an evergreen dream of the present computing era. Even the routine activities of day to day life can’t be imagined without digital assistance these days. The digital dependence is increasing rapidly, and so is the cyber-crime.
A cyber-attack has many different forms, and botnet is one among the top listed ones and is also regarded as the severe threat call to the IoT ecosystem, which is the backbone of digital communication. The bitter truth is that most of the IoT devices can be easily converted into IoT botnets and can be used as cyber weapons to destroy or break the IoT ecosystem.
What is a botnet?
Let us begin with understanding the term BOTNET. A Botnet is the fusion of two different words, robot and network. We all know that a Robot is the synonym of automation. So, a group of robots or any automated code in a web of systems to exploit the IoT environment is referred to as a Bot (Zombie Computers) or Botnet. With the help of command and control services that use different security protocols, these Botnets took over many forms from the traditional IRC to the recent advancements.
Botnets are always referred to as be a group of malware-infected systems controlled by a botmaster remotely and are targeted to implant the malicious code into different devices like computers, internet devices, mobiles, laptops, etc. The malicious attacks include the denial of service, data theft, unauthorized access, and send spam data. Client-Server Model and Peer-to-Peer Model are the two types of Botnet architectures identified to date. The existence of these Botnets has been discovered in the year 2000 itself, i.e., more than a decade ago, and the number of botnet attacks is increasing in a lightening manner whereas the countermeasures improvement is lagging behind.
How botnet attacks impact the IoT ecosystem?
The botnet has different attacking modes, and each way of attack has a different impact on the system. One of the most common attacks is DDoS.
Distributed Denial of Service
Ever wonder why your calls are not connected in the first attempt during New Year's Eve?
Why are your tickets not booked during the high thrust seasons in any travel platform?
The answer is simple; the server of the respective software is loaded heavily with a large number of users. Hence the system slows down occurs or you may have to wait for a significant amount of time for the software to be responsive again.
Similarly, when portrayed in a negative sense, in DDoS, the botnet tries to overload the target system by hitting the server continually with fake accounts or anonymous accounts which affects the system’s response timely initially and finally a breakdown occurs causing the authorized and other regular customers to face the accessing issues. This also leads to the closing of service temporarily by the affected systems or networks. The frequency of DDoS attack differs from one protocol to another protocol and also how long the system can be in infected mode is also different for each attack.
Let us consider the trending Mirai Botnet example to understand better about the subject.
Mirai has awakened the sleeping phase of security threats to a new model and has been one of the most hitting IoT threat with unexpected results. With the help of Mirai, hackers have created the spinoffs of various original malware and started attacking the target systems.
Open Telnet ports were the main cause for the rise of Mirai Botnet as they helped to login to various software with fake and default passwords causing a DDoS attack.
- The Mirai Botnet is one such malware that can convert the LINUX networking devices into remotely controlled Bots and can trigger the DDOS easily.
- The attack on Brian Krebs’ website, Dyn Cyber-attack and the OVH attack are some of the DDOS Mirai Botnet attacks
How to secure and safe-guard an IoT ecosystem?
The only way to protect and prevent cyber-attacks is to act alert. Especially when coming to IoT devices and networks, every single neglected issue can turn out as a weapon against you. The scope of the IoT ecosystem is so vast that the security methods should be altered and improved for every different type of device and network we use. Hence, after in-depth research and understanding, the following countermeasures can help you to overcome the Botnet attacks and also helps to immune your IoT ecosystem better than ever.
- A thorough understanding of Botnets, their impact, and training the resources accordingly can help to identify and prevent the botnet attacks easily and early
- A robust network must be designed which doesn’t allow the C&C protocols easily
- Use only trusted IoT devices, internet connection, and other networking operations
- Early detection of malware
- Stay-Update with security patches
- Monitoring the network behavior closely
- Anti –Bot mechanisms must be installed and updated regularly
Of all the above, Early detection of malware is the most important thing which enables you to react to the Botnet attack quickly before it entirely rules your system. A well-defined and secured website and its services is always a prior choice to all the customers and clients.