Imagine the present Digital world without the use of Computers…..Can’t, right? We are entirely dependent on computer usage either directly or indirectly to address both our personal and professional needs. But the fact is that there is always a high-risk exposure awaiting to thrash our systems and conquer the entire information without authentication by just injecting a small piece of malware into our systems.
Malware is a piece of code intended to harm the residing resource. Understanding and analyzing every aspect of a given malware like its origin, functionality, and the impact under special conditions can be coined as the definition for malware analysis. It is highly recommended to assess malware behavior and take the respective preventive measures.
Need for malware analysis
- To examine the malware behavior
- To determine the damages that can be caused
- To identify the cause of vulnerability
- To analyze and define the compromising indicators
- To analyze the impacts of the attack and identify the primary victim.
Types of malware analysis
Malware Analysis can be generally categorized into three different categories, as shown below.
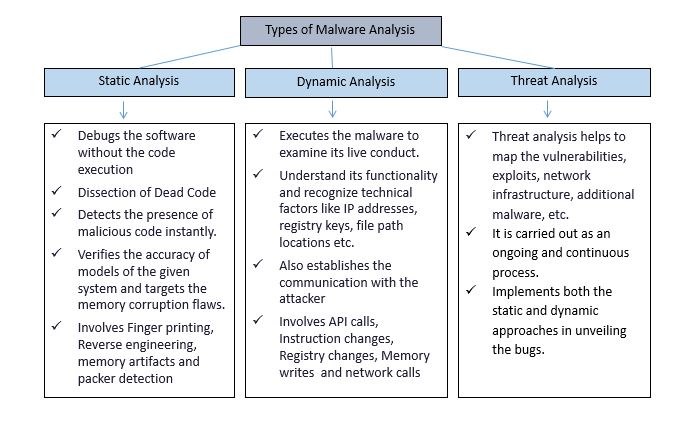
Static malware analysis techniques
#1. Analysis of memory and operating system
The memory and the operating systems must be thoroughly checked and verified frequently to investigate the new entries.
#2. Virus scan
A virus scan must be performed every time a new program or software is installed. Ensure to use only updated malware detecting software.
#4. Identify the Windows executable files
Examine and identify all the executable files residing in windows along with the associated compilers.
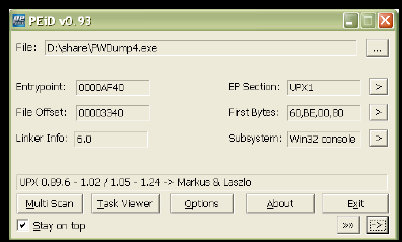
#5. Automate dis-assemblers
The Dis-assemblers can automate the code in a reverse manner and also upgrade its security levels.
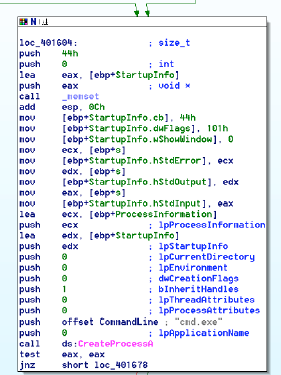
#6. File fingerprinting
Always ensure to fingerprint the files so that the value changes can be identified easily and quickly.
#7. Identify the packed code
Never ignore the packed code existence and try different identifying software to detect it. Completely bifurcate the point and click packers as they lay the path to the intruder to take control of the system.
#8. String analysis
Every string must be deeply analyzed to know its purpose function and where it is located in the file.
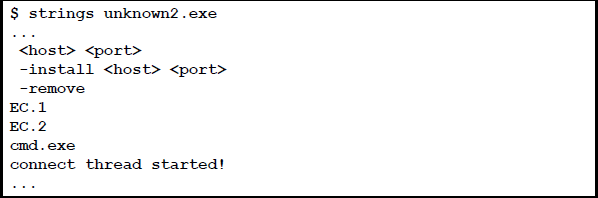
#9. Safeguarding web search
Be careful with the IP addresses, different domain names, network issues, and email addresses while browsing, and avoid any imprudence with malicious code.
Dynamic malware analysis techniques
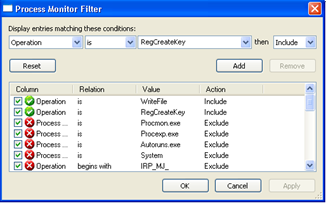
#1. Monitoring process and filtration
Process monitoring helps us to find the key attribute information like thread activity, process time, file activity, and registry activity. Filtration plays a vital role in monitoring.
#2. Analyze the network traffic
The next key factor of dynamic analysis is to detect the network traffic and to determine the prospects of it.
#3. Analyzing PE structure
Examine the PE file to identify interesting fields of code.
- .text: This contains the executable code.
- .rdata: This section holds read-only globally accessible data.
- .data: Stores global data accessed through the program.
- .rsrc: This section stores the resources that are required by the executable.
#4. Debugging
Dynamic linking and debugging always benefit in the early identification of malware and helps to attain protection.
